WannaCry, The Biggest Ransomware Attack Ever?
WannaCry, is it the biggest ransomware hacks ever? Well for one, it shut down some of the biggest employers of people in the world and also has a cheeky lil twist at the end of it. While it also caused whopping at least £6 billion worth of damage worldwide. So, have you ever had any hacks or fraud attempted on you?
Before we crack on we got a lot of info from the national UK audit office for big chunks of interesting facts, bbc.co.uk and acronis.com for a bunch of the detail in this story.
On May 12th 2017 a program called WannaCry, tore across the globe, infecting a quarter million machines in more than 150 countries. it affected NHS, Spain-based Telefonica (owner of O2 here in the uk), America’s FedEx, German railway company Deutsche Bahn, and LATAM Airlines. Making it one of, if not the largest ransomware attacks ever!
But what is ransomware?
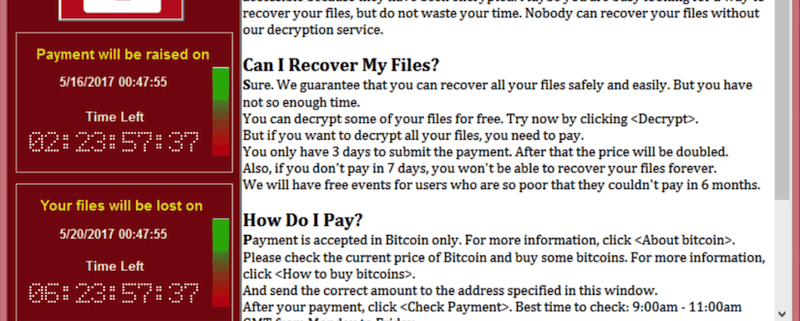
Ransomware is a type of malicious software that infects computer servers, desktops, laptops, tablets and smartphones, often spreading across networks to other devices. Once it compromises a system, it quietly encrypts every data file it finds, then displays a ransom note to the user demanding an online payment of hundreds or thousands of pounds (to be paid in cryptocurrency like Bitcoin) in return for the decryption keys needed to restore the user’s locked files. The demand often includes a series of deadlines for payment. Each missed deadline leads to a higher ransom demand and often, destroyed files. If the victim doesn’t pay up, the attacker discards the decryption keys, making the data permanently inaccessible.
Now what made Wannacry so dangerous? Well it attacked the NHS which is a big deal. As the NHS is a free healthcare service in the UK which has a LOT of peoples personal & medical data. Losing that data could, worst case scenario end up in death. It ended up costing us the UK £92 million and running up global costs of up to a whopping £6 billion.
Standstill
On Friday 12th May 2017, the NHS, was brought to a standstill for several days due to the WannaCry outbreak, spreading across and affecting hospitals and GP surgeries across England and Scotland. NHS staff shared screenshots of the WannaCry program, which demanded a payment of $300 (£230) in virtual currency Bitcoin to unlock the files for each computer.
Considering there are hundreds if not, 1000’s of computers across the whole of the NHS, this would prove costly. The attack resulted in the cancellation of thousands of appointments and operations, with one member of the public having his heart surgery cancelled.
Staff forced to revert to pen and paper and use their own mobiles after the attack affected key systems, including telephones.They also needed to take part in a last minute relocation of emergency patients from stricken emergency centres.
Why did it hit the NHS so hard though?
On Tuesday, March 14, 2017 a couple months before the attack, Microsoft issued a security bulletin, which detailed a in their systems flaw and announced that updates had been released for all Windows versions that were currently supported at that time.
The Department of Health was also warned about the risks of cyber-attacks on the NHS a year before WannaCry and although it had work under way it did not formally respond with a written report until July 2017 AFTER THE ATTACKS
Most of the NHS devices infected with the ransomware, were found to have been running, Microsoft Windows 7 operating system that was not up to date, hence the extremities of the cyber-attack. Yes that is right….the powers that be forgot to roll out a windows update. We are grossly oversimplifying the process here but that is what happened.
In fact At the time of the attacks, some computers were running a 17-year-old operating system (Windows XP). The attack happened in 2017 and windows xp was so old at the time windows had stopped updating it….in fact they stopped updating it in 2014. Luckily In an unusual move, Microsoft released a WannaCry patch for Windows XP. but this was after the fact.
Who was behind the attack?
Well it’s not too clear but here are some theories.
The attack used a software vulnerability in Microsoft’s Windows operating system called “Eternalblue”. Ironically, it was allegedly developed as a cyber-attack exploit by the US National Security Agency. Although they were reported to have known of the tool’s vulnerabilities, the NSA didn’t bring it to Microsoft’s attention until the hacker group called Shadow Brokers leaked EternalBlue to an obscure website.
Further analysis of the attack by companies such as Cyber Security company Symantec revealed links to a collective called the Lazarus group, who in turn have been linked to North Korea. However the attack does not bear the hallmarks of a nation-state campaign.
What stopped the attack?
A MARCUS DID!
The cyber-attack was stopped by an accidental kill switch discovered by Marcus Hutchins, Marcus was around 22/ 23 at the time did some digging around and found out how to turn it off. Plot twist – he was hailed a hero in the white hat (white hat means good hacker) hacking world!
All praise Marcus….Marcus the great….another in a long line of marcuses!
In august 2017 a few m months after the attack he was celebrating in LA after a hacker conference. Where lets face it…people must of been buying drinks for him all day long! He was arrested by the FBI. This was because a few years back he designed his own naughty bit of programming called Kronos in 2014. Kronos was made to stealing banking login credentials from people. It was sold for $7,000. He was also accused of being involved in the making of other similar programs as well. Yep the guy that saved the NHS could be responsible for that time your bank got hacked. But an older, wiser, better Marcus made the following statement in april 2019
“I regret these actions and accept full responsibility for my mistakes,”
“Having grown up, I’ve since been using the same skills that I misused several years ago for constructive purposes. I will continue to devote my time to keeping people safe from malware attacks.”
What happened afterwards?
The WannaCry attack triggered a boost in investment from the government for cyber security in the NHS. No surprise there…
Keep up to date with everything How To Kill An Hour by signing up to our newsletter by clicking here!
Let us know what you think of the show by clicking here!
Click here to subscribe to our YouTube Channel to see more amazing ways to kill time!
Follow us on Twitch by clicking here!